About
Welcome to the home page of the Australian Summer School on Privacy. This workshop will be held during 10-14 November 2025 at the University of New South Wales, Sydney, Australia.
The primary objective of the summer school is to promote research on Privacy Enhancing Technologies and associated research in Australia. It is a forum to bring together students, researchers, and practitioners in the broad area of privacy to learn, discuss, and collaborate on relevant questions and recent advances around privacy technologies.
The scope of the summer school includes, but is not limited to:
- Cryptographic Tools for Privacy
- Differential Privacy and Private Data Analytics
- Machine Learning and Privacy
- Privacy in the Age of AI
- Inclusive Privacy
- Management of Digital Identity and Credentials
The program will consist of two parts: keynote/invited talks in the mornings, and group discussions in the afternoons. For the group discussions, we plan to have several small groups, and for each group, we aim to gather researchers who are all interested in one specific topic. The goal of the group discussion is to advance collaborations within the research community and to find new results through discussions.
The workshop is open to PhD students, MPhil students, Post Docs, ECRs, academics and industry professionals. There are no registration fees. However, interested participants should express their interest by 20 October 2025 using this link: Expression of Interest Form. The selected list of participants will be notified at the beginning of November.
A limited number of students and early career researcher will be given stipend to attend the school. If you want to apply for a stipend, please refer to the Stipends section.
Other participants will have to arrange their travel and stay on their own. The workshop will provide free morning tea, lunch and afternoon tea.
Location
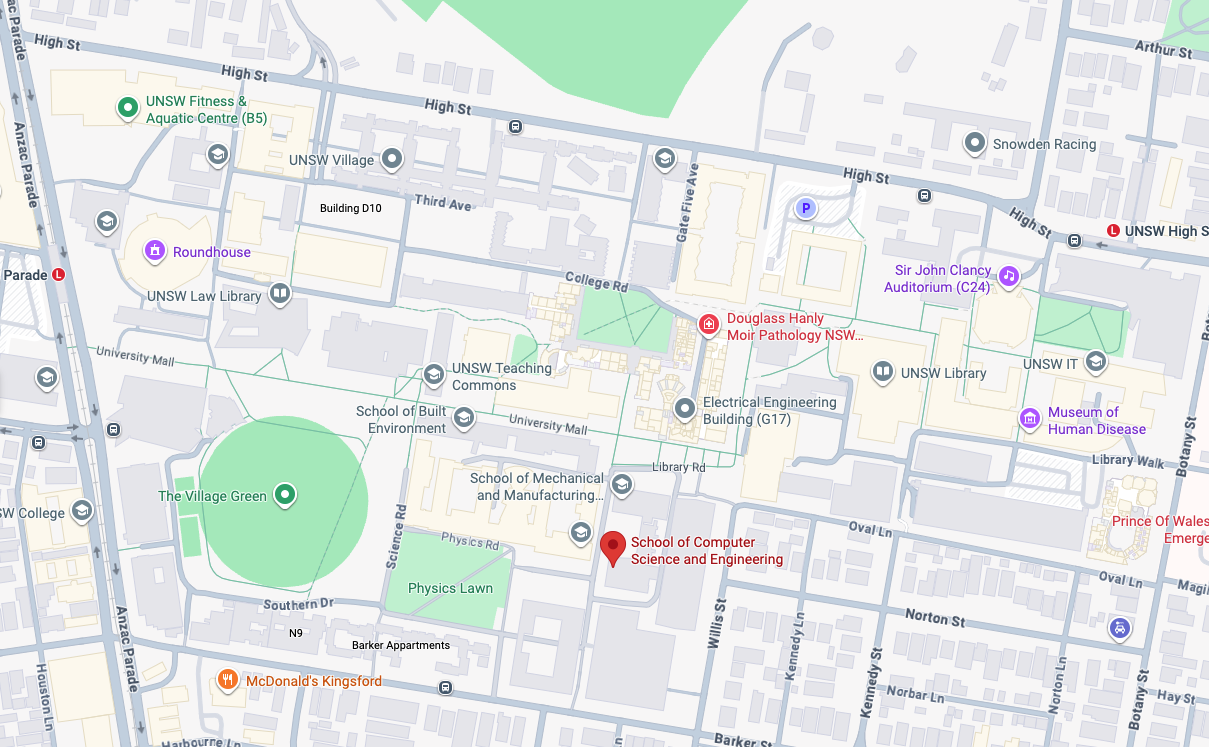
School of Computer Science and Engineering (Building K17)
Engineering Rd, UNSW Sydney
Kensington NSW 2031
Stipends
Applications are closed!
The stipend program is open to PhD students, MPhil students, and early career researchers. At this time, stipends can only be offered to participants from Australian institutions, i.e., only travel within Australia can be supported. Eligible participants can apply via the following form: Stipend Application Form.
Moreover, the recommendation from a supervisor or an academic mentor is required. The referring supervisor/mentor can upload their referral using the following link: Referral Form.
IMPORTANT: Students are responsible for ensuring that their supervisors/mentors submit their referral form by the deadline. Application without a referral will not be considered!
Deadlines
All deadlines are 23:59:59 AoE (UTC-12).
- Applications: 20 October, 2025 – Closed!
- Notification: 28 October, 2025
Speakers
-

Daniel Slamanig – Website
Daniel Slamanig is Full Professor of Cryptology at the Universität der Bundeswehr München (UniBw M), Department of Computer Science, and the Research Institute Cyber Defense (CODE), where he leads the Quantum Safe & Advanced Cryptography (QuSAC) Lab. He received his PhD in Computer Science from the University of Klagenfurt in 2011. Before joining UniBw M in 2023, he was a Senior Scientist in the cryptography research group at the AIT Austrian Institute of Technology (2017–2023), a lecturer at the Vienna University of Technology (2018–2020), and a PostDoc and later Senior Researcher at the Institute of Information Security (formerly IAIK) at Graz University of Technology (2012–2017). His research interests span the foundations and applications of cryptography, with a particular focus on provably secure public-key cryptographic primitives and privacy-preserving cryptographic mechanisms. He is a member of the International Association for Cryptologic Research (IACR) and the Association for Computing Machinery (ACM).
Universität der Bundeswehr München
-

Ming Ding – Website
Ming Ding (IEEE M'12-SM'17) received the B.S. (with first-class Hons.) and M.S. degrees in electronics engineering from Shanghai Jiao Tong University (SJTU), China, and the Doctor of Philosophy (Ph.D.) degree in signal and information processing from SJTU, in 2004, 2007, and 2011, respectively. From April 2007 to September 2014, he worked at Sharp Laboratories of China as a Researcher/Senior Researcher/Principal Researcher. Currently, he is the Group Leader of the Privacy Technology Group at CSIRO's Data61 in Sydney, NSW, Australia. Also, he is an Adjunct Professor at Swinburne University of Technology and University of Technology Sydney, Australia. His research interests include data privacy and security, machine learning and AI, and information technology. He has co-authored more than 300 papers in IEEE/ACM journals and conferences, all in recognized venues, and around 20 3GPP standardization contributions, as well as two books, i.e., “Multi-point Cooperative Communication Systems: Theory and Applications” (Springer, 2013) and “Fundamentals of Ultra-Dense Wireless Networks” (Cambridge University Press, 2022). Also, he holds 21 US patents and has co-invented another 100+ patents on 4G/5G technologies. Currently, he is an editor of IEEE Communications Surveys and Tutorials and IEEE Transactions on Network Science and Engineering. Besides, he has served as a guest editor/co-chair/co-tutor/TPC member for multiple IEEE top-tier journals/conferences and received several awards for his research work and professional services, including the prestigious IEEE Signal Processing Society Best Paper Award in 2022 and Highly Cited Researcher recognized by Clarivate Analytics in 2024.
CSIRO's Data61
-

Natasha Fernandes – Website
Natasha is a lecturer in Cybersecurity with special interests in privacy-preserving technologies and mathematical techniques for analysing information leaks in secure systems. She holds an undergraduate degree in Pure Mathematics and Computer Science from the University of Sydney, and a PhD in Computing from Macquarie University and École Polytechnique in France. Natasha has also worked extensively in industry as a software engineer specialising in backend web applications. Natasha's research interests are in the mathematical foundations of data privacy, particularly involving differential privacy, natural language processing or machine learning. Her work involves probabilistic reasoning using quantitative information flow techniques which derive from information-theoretic principles. Natasha's research aims at developing mathematical principles to support the analysis of privacy-preserving systems, as well as the development of software tools to support the application of these mathematical techniques in practical engineering scenarios.
Macquarie University
-

Nishanth Chandran – Website
Nishanth Chandran is a Senior Principal Researcher at Microsoft Research India. His research interests are in problems related to cryptography, secure computation, and AI security. Prior to joining MSRI, Nishanth was a Researcher at AT&T Labs, and before that he was a Post-doctoral Researcher at MSR Redmond. Nishanth is a recipient of the 2010 Chorafas Award for exceptional achievements in research and his research has received coverage in science journals and in the media at venues such as Nature and MIT Technology Review. He has published several papers in top computer science conferences and journals such as Crypto, Eurocrypt, IEEE S&P, CCS, STOC, FOCS, SIAM Journal of Computing, Journal of the ACM, and so on. His work on position-based cryptography was selected as one of the top 3 works and invited to QIP 2011 as a plenary talk. Nishanth has served on the technical program committee of many of the top cryptography conferences on several occasions and he holds several US Patents. Nishanth received his Ph.D. in Computer Science from UCLA, M.S. in Computer Science from UCLA, and B.E. in Computer Science and Engineering from Anna University. Nishanth is also a top ranking (A grade) All India Radio South Indian Classical (Carnatic) Violinist and has performed at international venues such as the Hollywood Bowl, Los Angeles (as part of legendary sitarist Late Pandit Ravi Shankar’s ensemble) and the Madras Music Academy, Chennai.
Microsoft Research
-

Sanchari Das – Website
Dr. Sanchari Das is a tenure-track Assistant Professor in the Department of Information Sciences and Technology at George Mason University (GMU), where she directs the Data Agency & Security (DAS) Lab and the Secure Realities Lab. The labs focus on human-centered, adaptive privacy and security in AI systems for critical socio-technical environments.
Her group's publications and collaborations appear in top venues across privacy, security, and trustworthy AI, and she has mentored 30+ students who have gone on to impactful careers. Her work has been presented at CHI, ASSETS, USENIX, NDSS, IEEE S&P, RSA, Black Hat, and Financial Cryptography, earning best-paper recognitions at CSCW, ICISSP, and IoTDI. She has secured funding support from the National Science Foundation (NSF), Google, Meta (Facebook), Cisco, and others including $1.9M+ in research funding.
Before joining GMU, Dr. Das was an Assistant Professor at the University of Denver, where she received the Distinguished Faculty Award and the Provost's Award for Excellence in Academic Advising. She holds a Ph.D. from Indiana University Bloomington and brings industry experience from American Express, Parity Technologies, and HCL.
George Mason University (IST)
-

Suranga Seneviratne – Website
Dr. Suranga Seneviratne is a Senior Lecturer and the Director of the Networked Systems and Security (NSS) Lab in the School of Computer Science at the University of Sydney. He received his PhD in Electrical Engineering from the University of New South Wales in 2015 and his Bachelor’s degree in Electronic and Telecommunication Engineering from the University of Moratuwa in 2005.
His research interests span computer networks, network security, and the application of artificial intelligence in security. He has authored and co-authored over 75 peer-reviewed conference and journal papers, including publications in top-tier venues such as WWW, TMLR, CVPR, MobiSys, and TMC.
Dr. Seneviratne has an extensive track record of leading industry- and government-funded research projects, supported by organisations such as the Australian Research Council (ARC), Google, the Defence Science and Technology Group (DSTG), the Department of Defence (DoD), the Office of National Intelligence (ONI), and Axiata Digital Labs. Since joining the University of Sydney in 2017, he has secured over $5 million in external research funding, including approximately $2.2 million in the past two years.
The University of Sydney
-

Thorsten Strufe – Website
Thorsten Strufe is Professor of IT Security at Karlsruhe Institute of Technology (KIT), adjunct professor at TU Dresden, and an internationally recognized expert in privacy, security, and large-scale distributed systems. He serves as Deputy Speaker of the Cluster of Excellence CeTI (Centre for Tactile Internet with Human-in-the-Loop) and is a principal investigator in major research initiatives including the German Competence Center for IT Security KASTEL. His research focuses on enhancing privacy and resilience in social networks and distributed systems, with a special interest in privacy-preserving, decentralized technologies that challenge the dominant data-collection models of today's digital platforms.
With over a decade of leadership in collaborative research, he has contributed to numerous national and international projects funded by the EU, German Research Foundation, and other agencies. His work spans interdisciplinary collaborations at the intersection of technology, ethics, and society, with projects addressing topics from secure communication and anonymous networking to user behavior and data protection in online environments.
He has authored and co-authored numerous publications in leading journals and conferences, and his research has been recognized with several best paper awards. Before joining KIT, he held academic positions at TU Dresden, TU Darmstadt, University of Mannheim, and EURECOM, shaping research and teaching in privacy and network security across Europe. He actively engages in global academic communities, fostering international partnerships and dialogue on building secure and trustworthy digital infrastructures.
Karlsruhe Institute of Technology (KIT)
-
Qiang Tang – Website
Qiang Tang is currently an Associate Professor in the School of Computer Science at the University of Sydney. From 2016-2020, he was an Assistant Professor at New Jersey Institute of Technology, and Director of the JACOBI Blockchain Lab. Before that, he was a postdoc at Cornell. His research spans broadly on applied cryptography and blockchain with works mostly appears in flagship security/crypto/distributed computing venues, including CRYPTO/EUROCRYPT/ASIACRYPT, CCS/SP/USENIX Sec/NDSS and PODC etc. He won a few awards including the SOAR Prize, MIT TR35, best paper awards (e.g., DSN25, ICDCS24, ASIACRYPT16) and research awards from Google, Oracle and multiple top blockchain foundations. He served as Program Co-Chair of PKC 2024.
The University of Sydney
-

Vanessa Teague – Website
Vanessa Teague's research focuses on election security and verification. In 2023 she received the IEEE Cybersecurity Award for Practice (with Stark, Blom and Lindeman) for her work on Risk Limiting Audits for preferential elections, which will now run in election audits in the State of Colorado. She has also made significant contributions to the security of elections in Switzerland and Australia, having identified a series of serious problems in the cryptography of the Swiss and iVote Internet voting systems, which (at least in the Swiss case) were corrected as a result of the discovery. Her team at the university of Melbourne demonstrated re-identification of public Medicare-PBS data, which led to significant changes in Australian government data sharing.
Her research work focuses on cryptographic analysis that has important implications for matters of public interest, particularly elections but also data privacy and other related topics. Her current main focus is Democracy Developers, which she founded in 2022 to translate these ideas into open-source software supporting Australian democracy.
Thinking Cybersecurity / The Australian National University
Schedule
All rooms are located in the School of Computer Science and Engineering (Building K17).
Monday, November 10
| Time | Slot | Description |
|---|---|---|
| 8:45 – 9:30 | Registration & Coffee | Location: CSE Seminar Room (113) |
| 9:30 – 11:00 |  Privacy Foundations
Thorsten Strufe
Privacy Foundations
Thorsten Strufe | Location: CSE Seminar Room (113)TBD |
| 11:00 – 11:15 | Coffee Break | Location: CSE Seminar Room (113) |
| 11:15 – 12:30 |  Cryptography for Privacy
Daniel Slamanig
Cryptography for Privacy
Daniel Slamanig | Location: CSE Seminar Room (113)Cryptography offers important theoretical foundations for achieving privacy in the digital world. This talk provides an overview of the main cryptographic tools that enable computation and communication without revealing sensitive data, including secure multi-party computation, homomorphic encryption, and zero-knowledge proofs. We will see how these primitives allow data and computations to be verified and shared securely while preserving both confidentiality and authenticity, illustrated through examples. Finally, the talk highlights recent advances and open challenges in making these privacy-preserving techniques practical and scalable. |
| 12:30 – 13:30 | Lunch | Location: CSE Seminar Room (113) |
| 13:30 – 14:30 |  Introduction to Differential Privacy
Natasha Fernandes
Introduction to Differential Privacy
Natasha Fernandes | Location: CSE Seminar Room (113)Differential privacy (DP) offers a mathematically rigorous framework that is the gold standard for privacy in the current literature - but what is it and how does is work?This talk introduces the core principles of differential privacy, including its mathematical properties and some key DP mechanisms. We will look at some common applications of differential privacy and examples of privacy analyses used to prove DP properties. Finally, we will discuss the privacy-utility trade-off and touch on some open questions in the community. |
| 14:30 – 15:00 | Coffee Break | Location: CSE Seminar Room (113) |
| 15:00 – 16:30 |  Group Discussion
Group Discussion
| Location: CSE Seminar Room (113) , Room 401 , Room 501Interactive discussion in topic-specific breakout groups. |
Tuesday, November 11
| Time | Slot | Description |
|---|---|---|
| 9:30 – 11:00 |  AI/ML Privacy & Network Privacy
Suranga Seneviratne
AI/ML Privacy & Network Privacy
Suranga Seneviratne | Location: CSE Basement (B01)TBD |
| 11:00 – 11:15 | Coffee Break | Location: CSE Basement (B01) |
| 11:15 – 12:30 |  Towards End to End Encrypted Online Collaborations
Qiang Tang
Towards End to End Encrypted Online Collaborations
Qiang Tang | Location:
CSE Basement (B01)Despite the pervasiveness of cloud platforms that facilitate outsourced storage and online collaborations, the basic requirement of end-to-end security is not yet available. As a consequence, we've witnessed many massive scales data breaches, frequently. This is in sharp contrast with communication, that there are long sequences of research and practical systems for end-to-end encrypted messaging available. In this talk, I will overview the key challenges causing this mismatch, and our recent efforts of providing end-to-end security for cloud storage and Git services with rigorous guarantees, while preserving full compatibility with existing infrastructure, and incurring only minimal overhead. |
| 12:30 – 13:30 | Lunch | Location: CSE Basement (B01) |
| 13:30 – 14:30 |  Building Trustworthy Machine Learning Pipelines: Threats and Mitigations
Nishanth Chandran
Building Trustworthy Machine Learning Pipelines: Threats and Mitigations
Nishanth Chandran | Location: CSE Basement (B01)Machine learning systems increasingly handle sensitive data and operate in complex environments. This talk provides an overview of the core security and privacy challenges in modern ML, including threats to data and models, and discusses foundational approaches to mitigating these risks. |
| 14:30 – 15:00 | Coffee Break | Location: CSE Basement (B01) |
| 15:00 – 16:30 |  Group Discussion
Group Discussion
| Location: CSE Basement (B01) , CSE Seminar Room (113)Interactive discussion in topic-specific breakout groups. |
Wednesday, November 12
| Time | Slot | Description |
|---|---|---|
| 9:30 – 11:00 |  Building Trust in AI: Responsible Data Use, Risk, and Regulation
Ming Ding
Building Trust in AI: Responsible Data Use, Risk, and Regulation
Ming Ding | Location: CSE Basement (B01)This talk explores what it means to use data responsibly in the age of AI. We'll unpack common myths about AI and data usage, examine emerging risks in AI systems, and discuss how regulatory and technical approaches can work together to build trust. Drawing on recent national initiatives and research at CSIRO's Data61, the session highlights practical strategies for protecting sensitive data while supporting innovation and public confidence in AI. |
| 11:00 – 11:15 | Coffee Break | Location: CSE Basement (B01) |
| 11:15 – 12:30 |  Privacy for electronic elections
Vanessa Teague
Privacy for electronic elections
Vanessa Teague | Location: CSE Basement (B01)TBD |
| 12:30 – 1:30 pm | Lunch | Location: CSE Basement (B01) |
| 13:30 – 14:30 |  Panel: Bringing Privacy Research to Reality
Panel: Bringing Privacy Research to Reality
| Location:
CSE Basement (B01)Moderator: Salil S. Kanhere Panel: Ming Ding, Daniel Slamanig, Thorsten Strufe, and Vanessa Teague |
| 14:30 – 19:00 |  Social Event
Social Event
| Social event, will be communicated to the participants soon. |
Thursday, November 13
| Time | Slot | Description |
|---|---|---|
| 9:30 – 11:00 |  Privacy in Context: Models, Measures, and Design
Sanchari Das
Privacy in Context: Models, Measures, and Design
Sanchari Das | Location: CSE Basement (B01)This talk presents privacy as a contextual and human-centered concept, exploring how people understand and manage it in digital environments. It introduces the APCO model linking antecedents, privacy concerns, and outcomes, and discusses frameworks such as CFIP and IUIPC for measuring privacy attitudes and behavior. The session explains factors influencing privacy decisions including awareness, culture, demographics, and personality, and examines the privacy paradox, where concerns do not always reduce disclosure. It also outlines the role of trust, risk, and perceived benefit in privacy calculus and emphasizes the need for privacy by design approaches that embed fairness, transparency, and user control in technology. |
| 11:00 – 11:15 | Coffee Break | Location: CSE Basement (B01) |
| 11:15 – 12:30 |  Privacy of behavioral and biometric data
Thorsten Strufe
Privacy of behavioral and biometric data
Thorsten Strufe | Location: CSE Basement (B01)TBD |
| 12:30 – 13:30 | Lunch | Location: CSE Basement (B01) |
| 13:30 – 14:30 |  Attack Models for Differential Privacy
Natasha Fernandes
Attack Models for Differential Privacy
Natasha Fernandes | Location: CSE Basement (B01)Differential privacy (DP) is often regarded as a powerful privacy definition due to its strong attacker model and independence from prior knowledge. In this talk I will introduce some techniques for attack modelling and discuss how DP's attacker model sits in the landscape of these attacks. We will model other attackers and discuss how DP defences stack up against these. Finally, we will discuss strengths and weaknesses of the DP attack model, and identify gaps in the literature regarding privacy attacks. |
| 14:30 – 15:00 | Coffee Break | Location: CSE Basement (B01) |
| 15:00 – 16:30 |  Group Discussion
Group Discussion
| Location: CSE Basement (B01) , CSE Seminar Room (113)Interactive discussion in topic-specific breakout groups. |
Friday, November 14
| Time | Slot | Description |
|---|---|---|
| 9:30 – 11:00 |  Anonymous Credentials: Past, Present and Future
Daniel Slamanig
Anonymous Credentials: Past, Present and Future
Daniel Slamanig | Location: CSE Basement (B01)Anonymous credentials are an important cryptographic concept, envisioned in the 1980s by Chaum, to enable privacy-friendly authentication. In recent years, they have experienced renewed interest, driven by new applications and increased attention from industry. In this talk, we will review the basic concept, explore different properties and types of such schemes, and examine current constructions of anonymous credentials. We will also take a look into the future — specifically the post-quantum setting — and discuss open research problems. |
| 11:00 – 11:15 | Coffee Break | Location: CSE Basement (B01) |
| 11:15 – 12:30 |  Privacy Boundaries
Sanchari Das
Privacy Boundaries
Sanchari Das | Location: CSE Basement (B01)This talk explores how individuals manage privacy across social media, data-driven services, and digital ecosystems through adaptive boundary regulation. It introduces a five-part model addressing relationship, network, territorial, disclosure, and interactional boundaries, and explains user strategies such as filtering, blocking, withdrawal, and compromise. The session highlights challenges including the privacy paradox, imagined audiences, and context collapse, showing how these shape disclosure and control online. It also discusses privacy in healthcare and genetic data to illustrate stakeholder responsibilities and the need for multi-layered protection. The talk concludes with design principles for usable, trustworthy systems that uphold user agency, consent, and equitable data practices. |
| 12:30 – 13:30 | Lunch | Location: CSE Basement (B01) |
| 13:30 – 14:30 |  Presentations of Group Discussion Outcomes
Presentations of Group Discussion Outcomes
| Location: CSE Basement (B01)Each group presents key insights from their discussions. |
| 14:30 – 15:00 | Coffee Break | Location: CSE Basement (B01) |
| 15:00 – 16:30 |  Event Closing
Event Closing
| Location: CSE Basement (B01) |
Organisers
Organisers
- Sushmita Ruj, University of New South Wales, Australia
- Salil Kanhere, University of New South Wales, Australia
Local Organizations
- Gustavo Batista, University of New South Wales, Australia
- Rahat Masood, University of New South Wales, Australia
- Sara Ballouz, University of New South Wales, Australia
Web-chair
- Erik Buchholz, University of New South Wales, Australia
Contact
If you have any questions, please contact us at privacy-summer-school@cse.unsw.edu.au.